BalaBit IT Security, one of the global leaders in developing privileged activity monitoring, trusted logging, and proxy-based gateway technologies, announced the “Top 6 list of the most popular prohibited activities in the workplace among IT staff” as a results of its survey. The survey revealed that in spite of the fact that 74% of the interviewed IT professionals have already misused the company’s IT system, and could have lost their job, if a video recording could have proven wrongdoing, 92% of those surveyed would not object to being observed by an activity monitoring tool. The reason is that almost half of the IT staff needs to share user names and passwords for some server administration tasks, and 41% of them were already in a situation where it would have been beneficial if there had been a detailed video of their work.
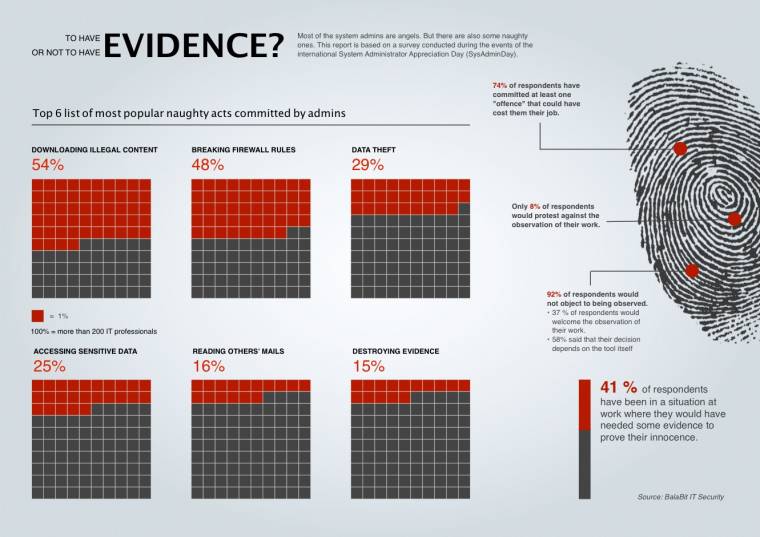
According to BalaBit’s survey, 74% of the IT staff have already misused the company’s IT system, and could have lost their job, if a video recording could have proven wrongdoing. Most of those found breaking company IT policies admitted to multiple offences. The survey shows an average of two offences per person. Only 36% of IT staff state that they have never tried any of the following activities.
Top 6 list of prohibited activities in the workplace among IT staff:
1. 54% of those interviewed said that have already downloaded illegal content in their workplace
2. 48% of them answered that they have made exception rules in the firewall or in other IT systems for personal purposes, to get around the IT policy
3. 29% of them “have taken home” company details
4. 25% have looked into confidential files, stored on the company’s server (e.g. list of salaries)
5. 16% have read their colleagues email (without the colleague’s permission)
6. 15% have already deleted or modified log files (in order to hide or destroy evidence)
Supporting quote
Zoltán Györkő, Business Development Director at BalaBit IT Security said: “Implementing an activity monitoring solution, which controls and monitors privileged users’ (such as system administrators, high level managers and employees working with sensitive data or outsourcing services providers) activities, will be inevitable in the near future, not only among the bigger enterprises but middle size organizations as well. Gartner recently published its “Top 10 Strategic Technologies for 2012" and predicted* an increasing number of smartphones and tablets will be used by employees, as well as the potential for broad, long-term impact of cloud computing in most industries. Both of these trends require a new approach to IT security strategies, one enabling real-time control of user access to the IT system, tracking of activities and the ability to report who had access to which sensitive content and what changes were made and by whom to mission critical IT systems. An activity monitoring tool helps companies passing compliance audits as well as protects the privileged users.”
Although no one likes to be observed during work – even if they have previously been informed about it – controlling privileged users’ activities is mandatory because of industry- and compliance regulations. For instance, financial institutions need to meet Basel III, the Markets in Financial Instrument Directive (MiFID II), the Market Abuse Directive, SOX-EuroSox, PCI DSS and several other standards forcing the adoption of IT controls such as ITIL, COBIT or ISO 27001/27002. Passing these audits successfully is required for organizations to continue everyday operations and prevent financial losses and damage to the company’s reputation.
Unique situation of the IT staff: 92% of them would not object to being observed
Because of this contradiction BalaBit’s research also examined how employees feel about implementing such an activity monitoring tool which can track all their activities in the IT system during work. Would they protest against a monitoring system, even if the success of the audit and business continuity depended on it? Or would they rather support the implementation, even if it meant that their work was observed and every mistake and the responsible person could be reported? According to the survey, only 8% of respondents indicated that they would strongly protest against implementing an activity monitoring solution, the remaining 92% would welcome (34%) or – depending on the tool itself – would not mind (58%). Why?
An activity monitoring tool protects the system administrators
Among privileged users, system administrators and outsourcing partners more often find themselves in a difficult position as they share user names and passwords for some server administration tasks. The recently announced Password 2011 survey of Lieberman Software Corporation revealed that 42%** of the IT staff are sharing passwords or access to systems or applications in their organizations. BalaBit believes that this is the reason why 92% of IT staff would not object to being observed as in case of any incident, it is difficult to assign blame if multiple users share passwords. Privileged users have personal interest in finding who is responsible for the costly downtime of the IT system. BalaBit’s survey result clearly shows that 41% of the IT professionals were already in a situation where it would have been beneficial if there had been a detailed video of their work.
About the survey
BalaBit IT Security has conducted this survey between July and October 2011 and interviewed more than 200 IT professionals (CIO’s, CSO’s, system administrators, system managers and other IT workers) in Central and Eastern Europe. Questionnaires were filled in anonymously, among Hacktivity Conference and System Administrator Appreciation Day participants as well. 51% of respondents work for large, 17% for middle size, 25% for small size companies. They are mainly from IT and telecom (53%), financial (24%), government (12%), retail (7%) and manufacturer (4%) sectors.
